Geotagging Cyberattacks
Amid global political instability, the number of state-backed cybercriminals and cyberattacks is rising. State-backed hackers often target companies that are under the jurisdiction of an adversary state and contribute to its economy. Such attacks inflict more damage than regular cyberattacks, as they are more well-funded and more sophisticated.
The connections between specific hackers and the government are not always clear. However, identifying the origin of hacker attacks is key. We believe that by establishing the locations of hackers and their victims, one can identify whether the hackers’ actions are politically motivated.
Current cybersecurity solutions are imperfect and typically rely on detecting the IP address and physical location of the hacker’s server IP. However, cybercriminals can avoid detection with this approach by obfuscating technologies such as VPNs.
Geotagging Hackers
For this blog post, we took an alternative approach. We utilized Geotagging AI ’s text-based geolocation models to identify the locations of hackers based on the text posted on their social media accounts. Below are the models’ predictions for three hacker groups.
- Stormous is a hacker group that is believed to have started operating in mid-2021. Stormous claimed responsibility for the attacks on big companies such as Coca-Cola. They previously admitted their objective to attack several Western European countries, and recently Ukraine. The group is actively posting on their Telegram channel.
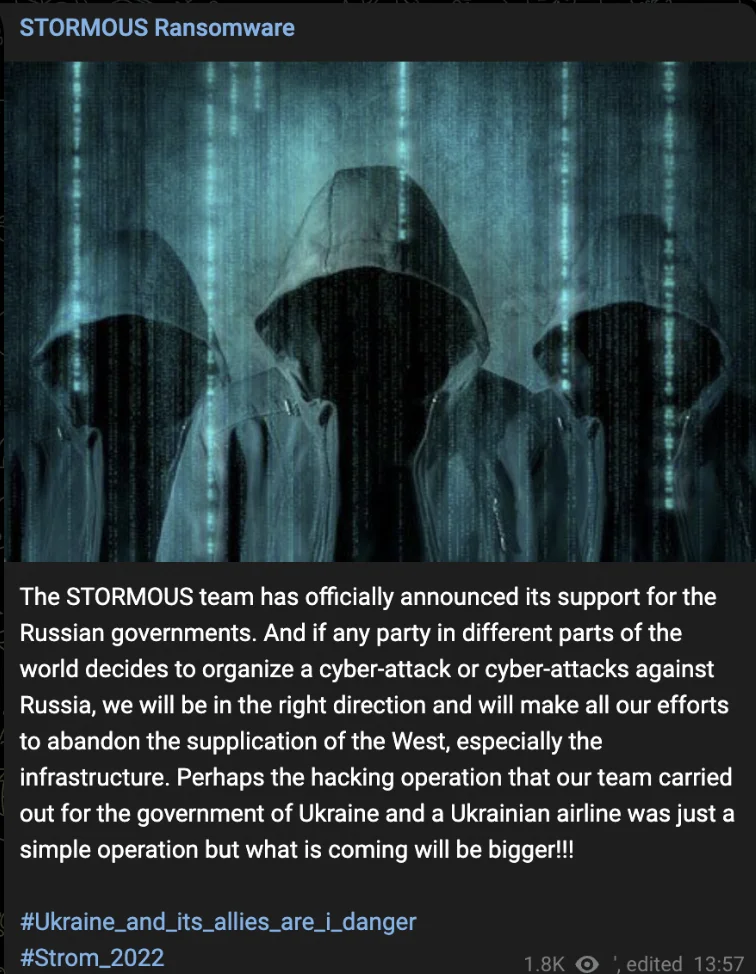
Screenshot of a message from Stormous Telegram channel
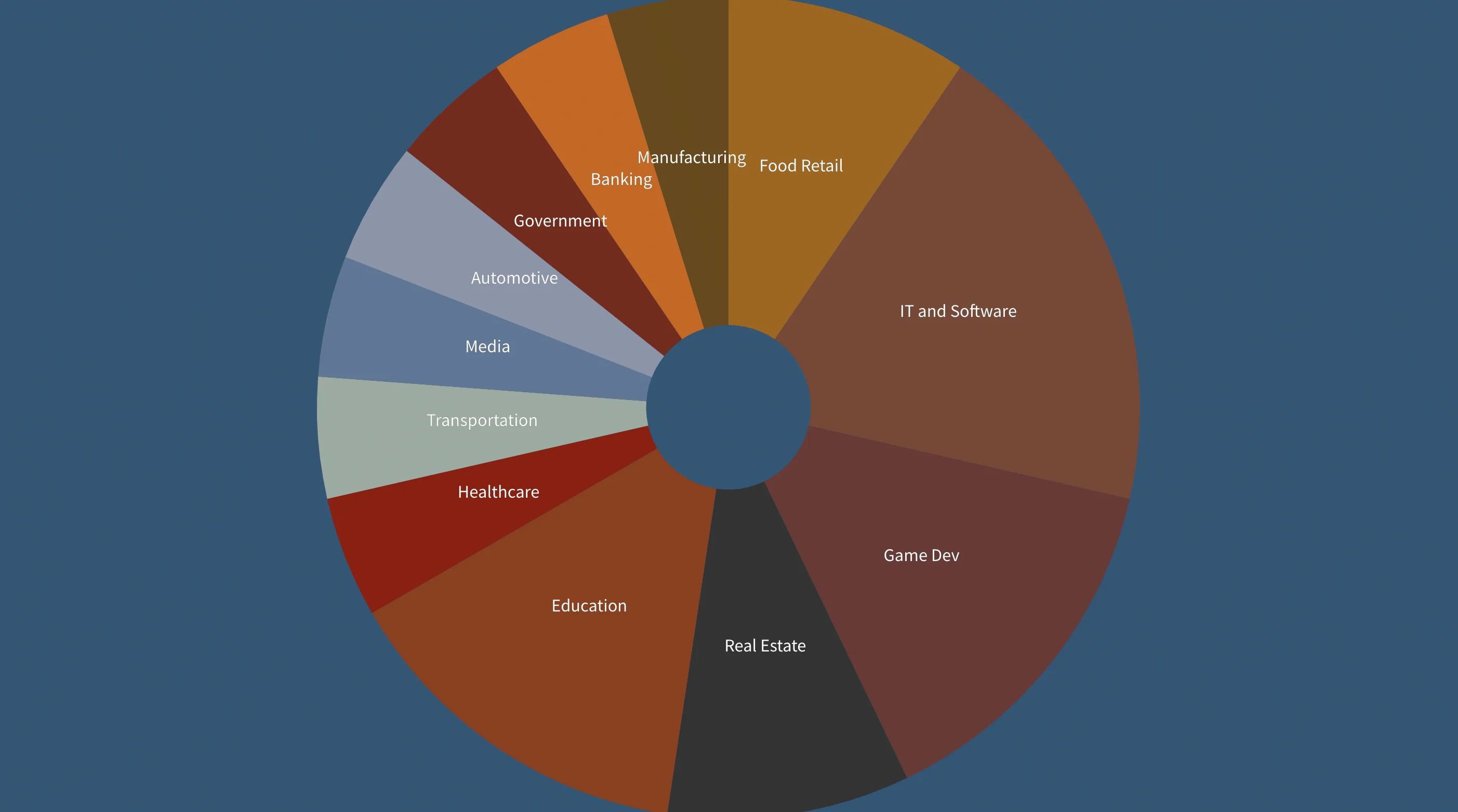
Companies hacked by Stormous, Count by Industry

Map of Stormous’ Victims
- Karakurt is another threat actor and is believed to have emerged in late 2021. The group steals data and then demands a ransom, threatening to release the information to the public. Karakurt has a number of suspended Twitter accounts and a Telegram channel where they advertise the leaked data they’ve stolen.
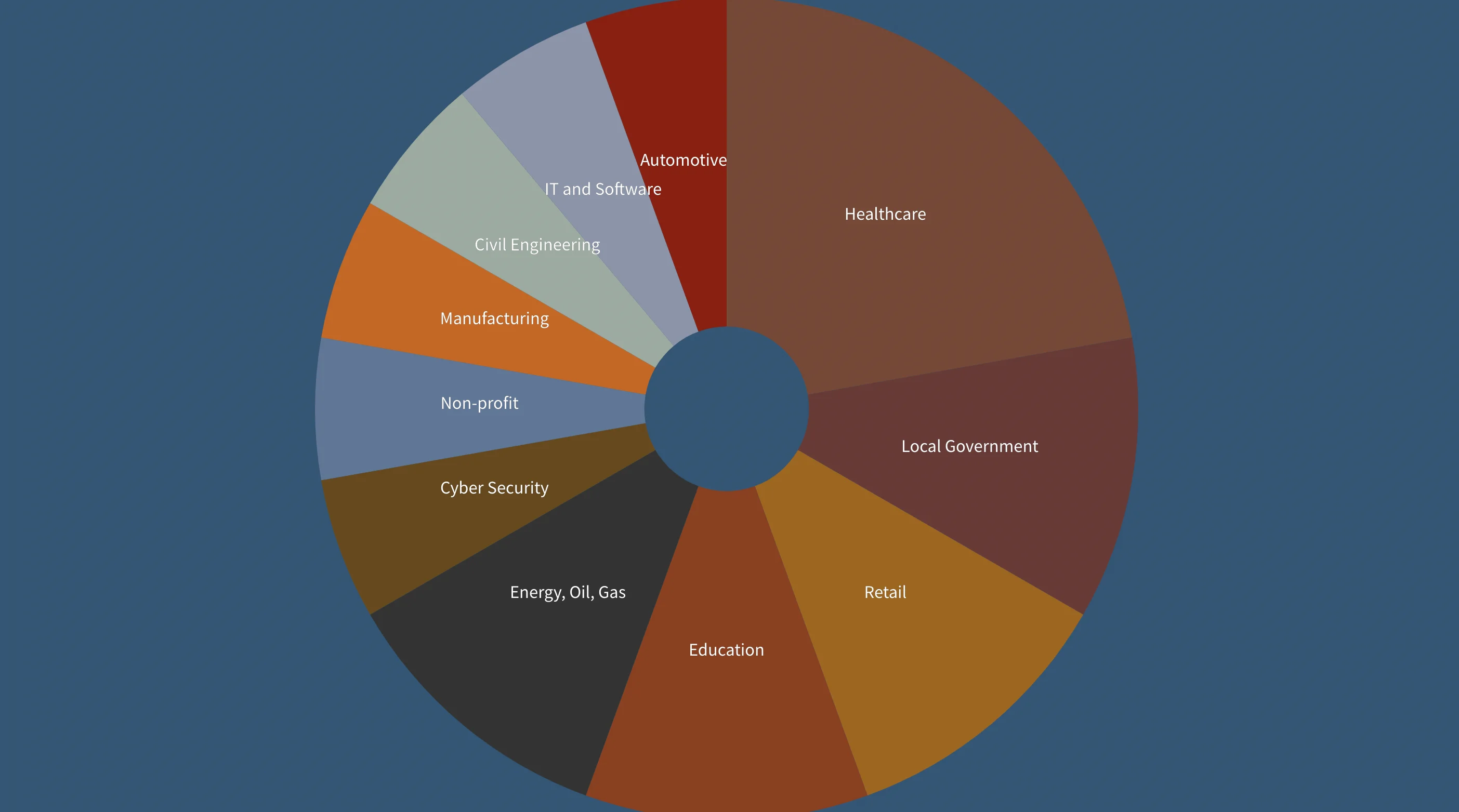
Companies hacked by Karakurt, Count by Industry
Most of Karakurt’s victims are located in the United States and Europe.
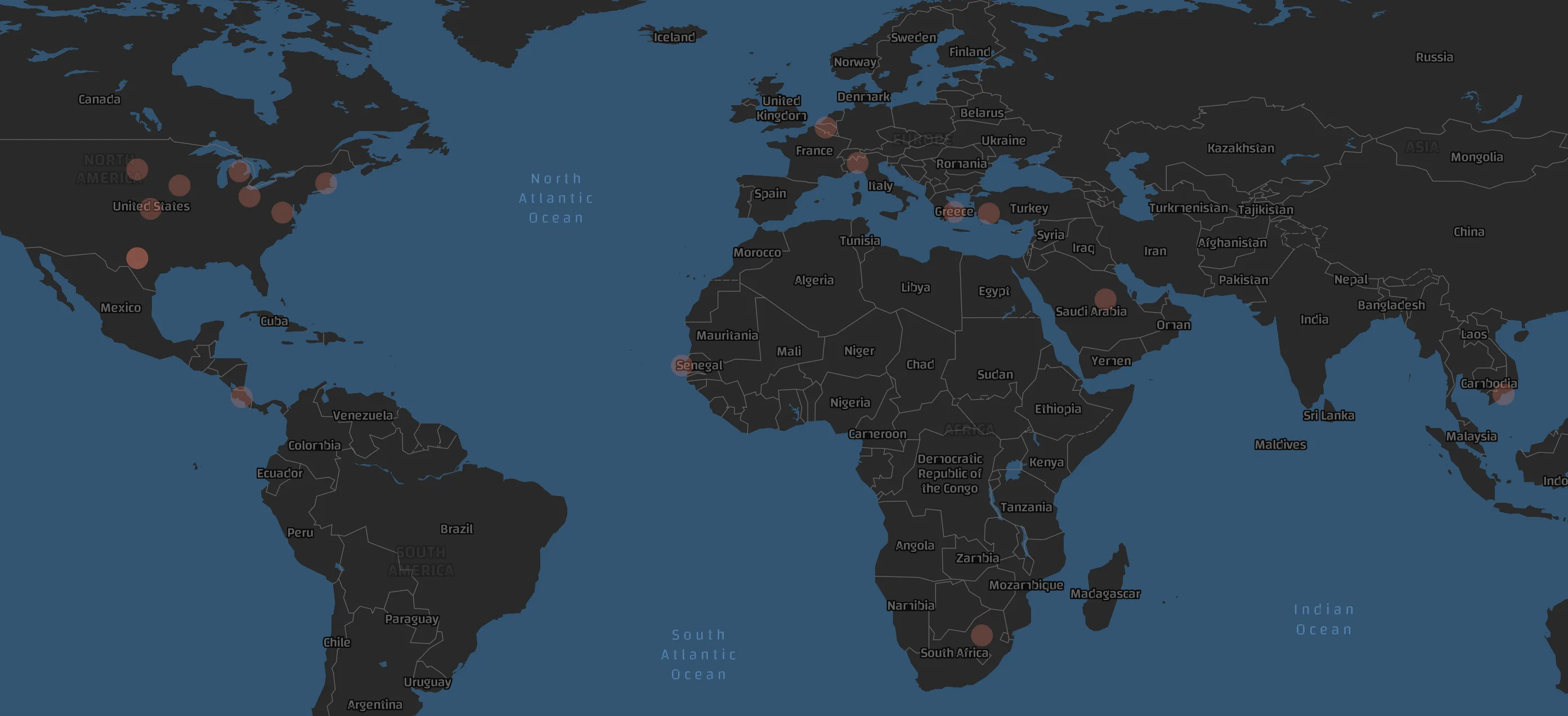
Map of Karakurt’s Victims
- Snatch Team is a ransomware group that uses the double-extortion technique. The group takes advantage of weaknesses in their potential victims’ infrastructure and coerces them into paying a ransom. In addition to their Tor website, the group frequently utilizes their Telegram channel to provide updates on the companies that they have breached.
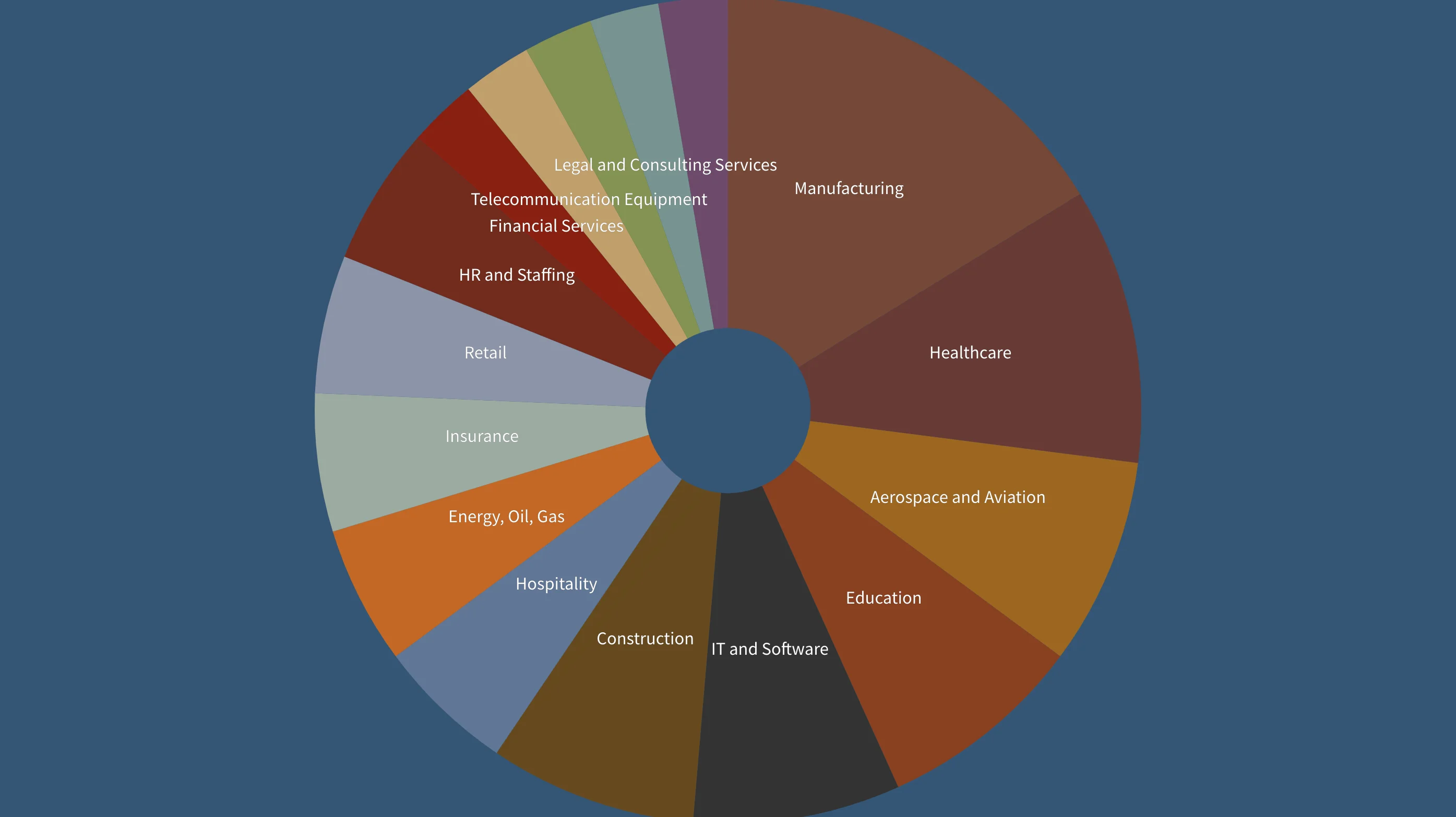
Companies hacked by Snatch Team, Count by Industry
As can be seen from the screenshot below, most of Snatch Team’s victims are US-based companies.
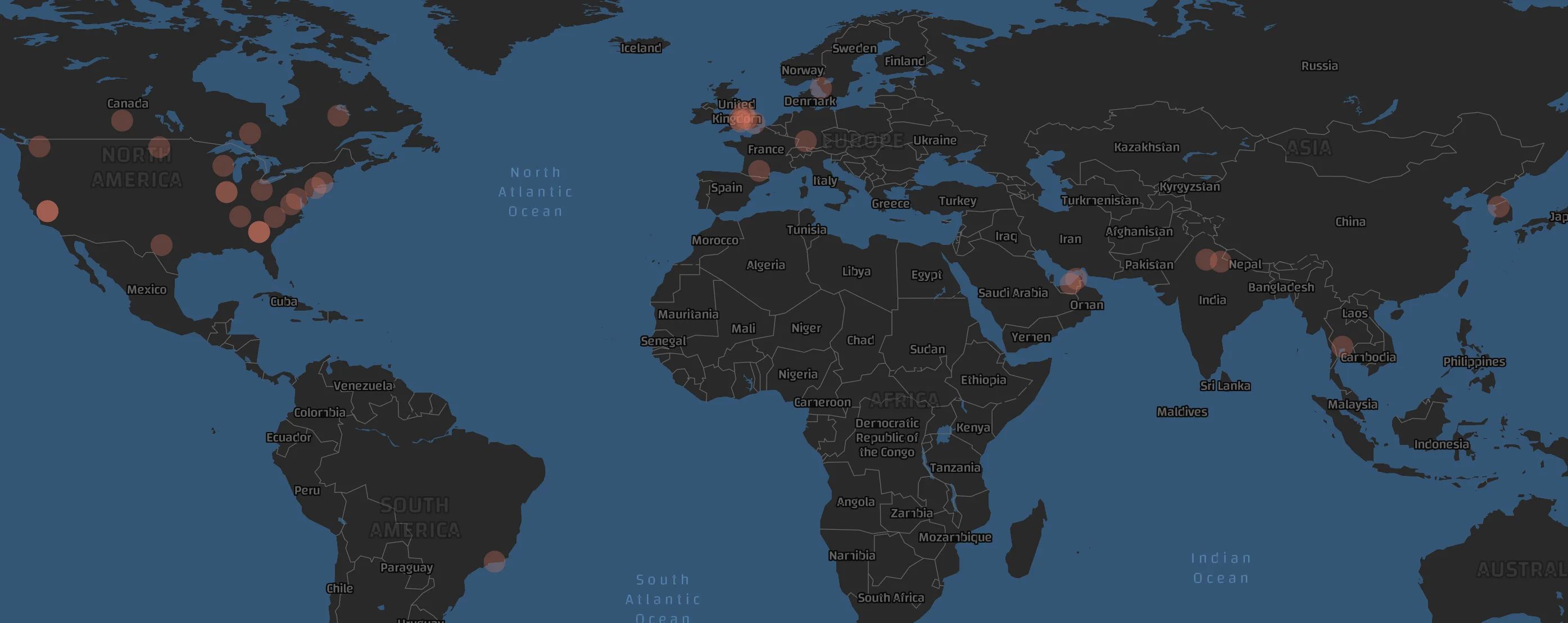
Map of Snatch Team’s Victims
The Geotagging AI model utilizes deep learning to make a geolocation prediction based on the post’s language, dialect, hashtags, etc.
The model’s prediction traces the location of all three aforementioned hacker groups back to the Commonwealth of Independent States (CIS) and former-CIS countries. The model does not provide a prediction that can be attributed with 100% certainty to a single country, but rather to the former CIS region as a whole.
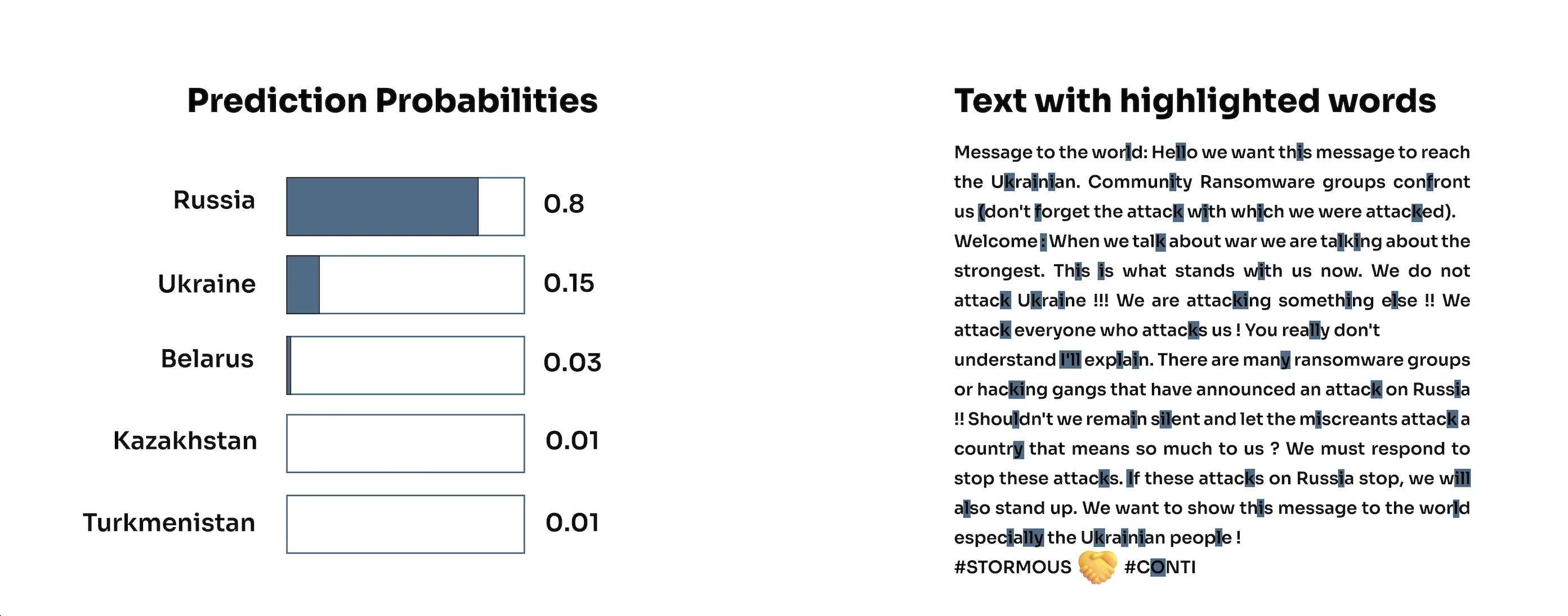
Geotagging AI Model – Clusters
Though the model’s predictions are not completely definitive, they provide some valuable insights into the correlation between the political agenda of CIS countries and the locations of the victims of all three hackers.



